Privacy and Security

PhoneGap Day EU - 2017
for PhoneGap developers
Privacy
Security
vs.
What is their relationship?
-
One does not always guarantee the other
-
Security doesn't always keep data private
-
Privacy is also a security issue
-
attack vectors, etc
-
Security and Privacy go Hand in Hand 👬
Strong Privacy Needs Security
Without good security, Privacy cannot be protected from those with malicious intent
“Hack Yourself First”*
Better you than someone else...
Fun resource: http://hackyourselffirst.troyhunt.com
What Kinds of Attacks might be Mounted Against a PhoneGap app?
-
Direct API or Server Access
-
Cross Site Scripting (XSS)
-
Cross Site Request Forgery (CSRF)
-
SQL Injection
-
MitM
-
Broken Auth and Session Management
-
User Exploitation (Phishing, etc)
-
Etc…
Pretty much the same as those used to attack Browser apps
As we say in Australia:
"Yeah, Nah"*
Is Hacking Hard?
Does it take "mad skillz"?
* Sadly and confusingly, that means “No”


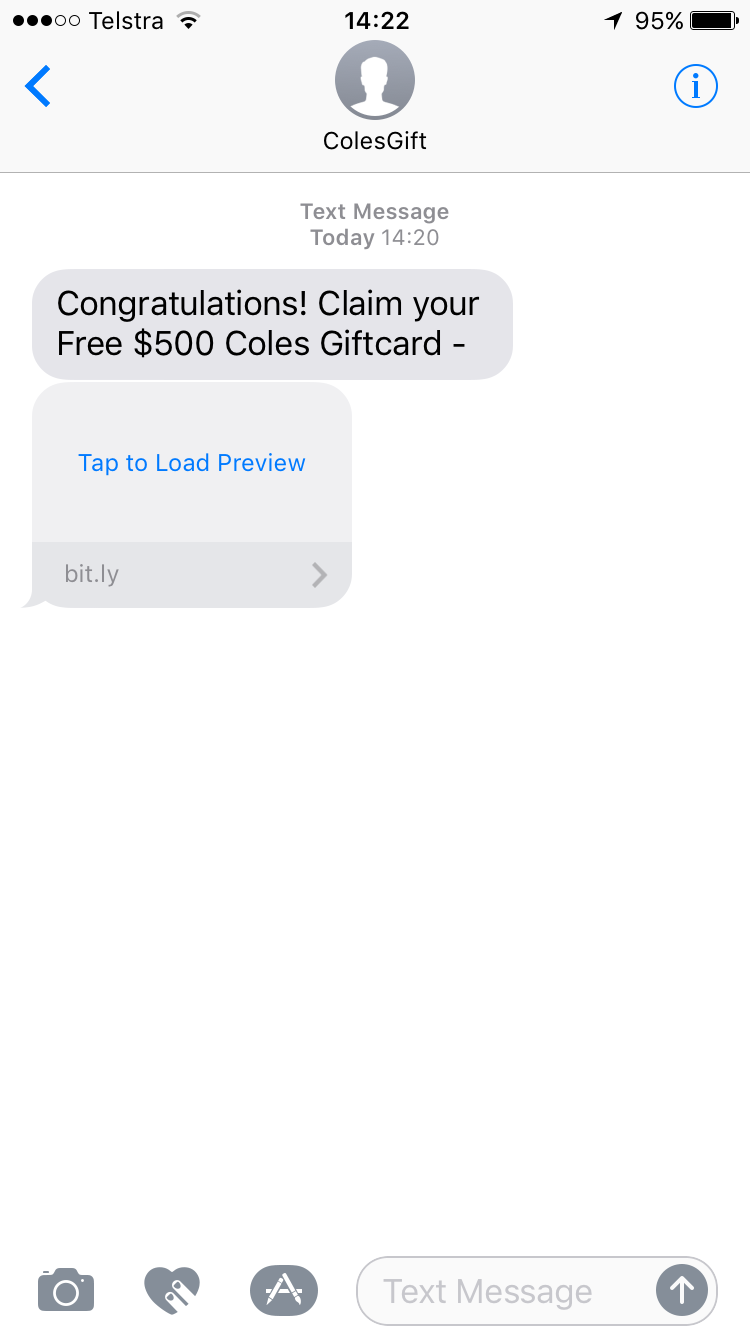
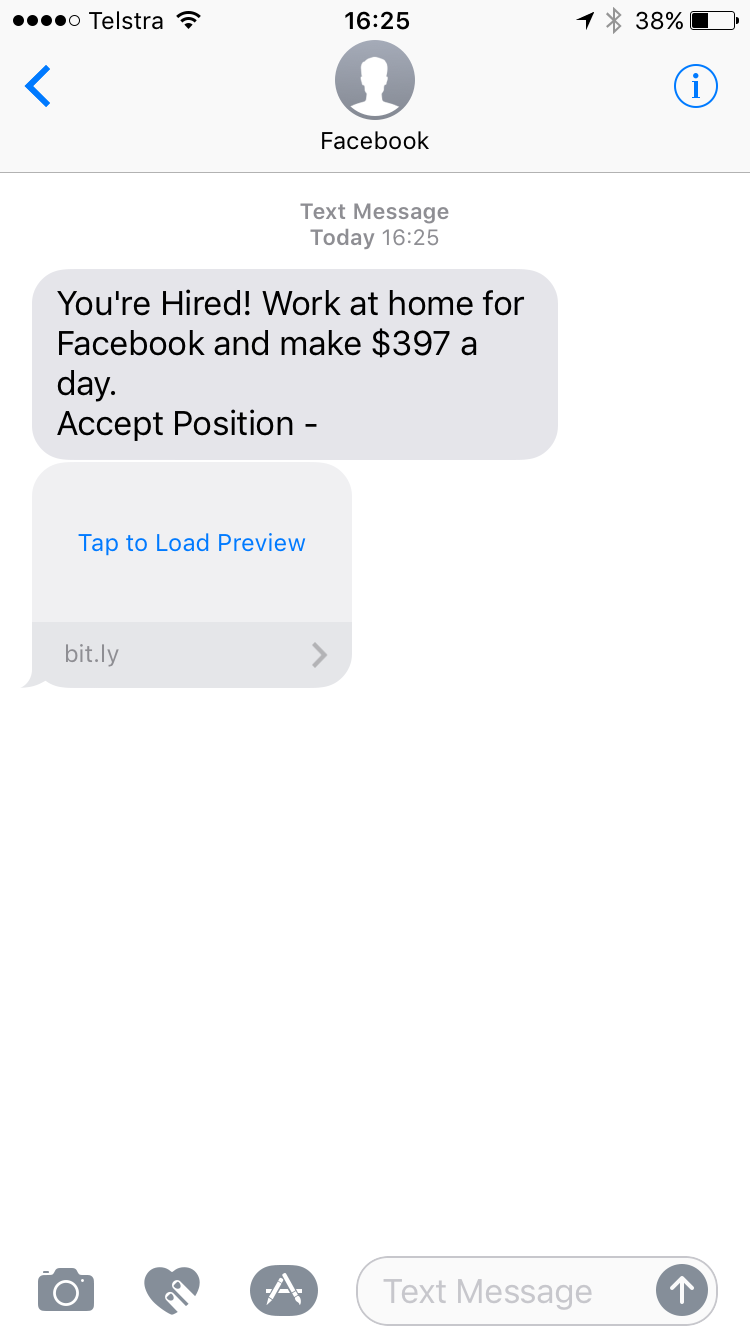
Be sure to compliment my wife on her new job at working from home at Facebook

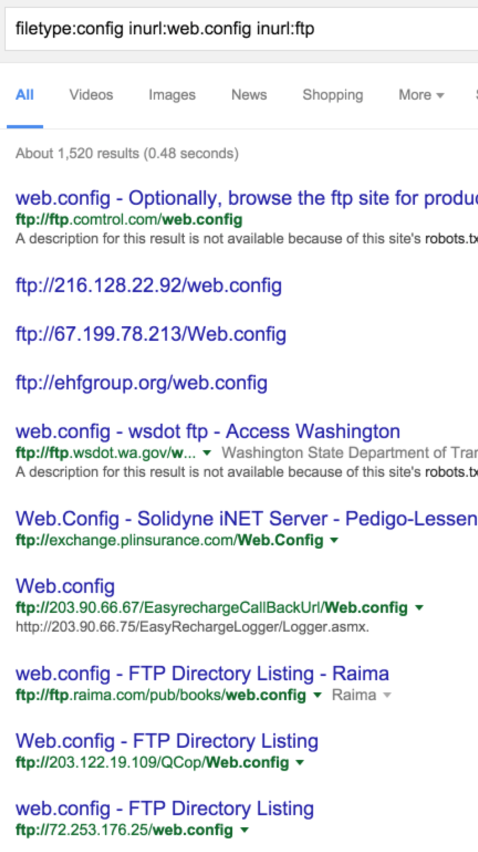
Google Dorks
Who are you calling a dork…
ya dork?
Not going to bother demoing this, you get the idea
Plenty of hacking tools
Don’t require advanced knowledge
Pixfor
OK, So what are we going to hack on today?
...the vulnerable edition
Running the app
-
$ git clone https://github.com/devgeeks/pgdayeu-pixfor
-
$ cd pixfor-vulnerable/app
-
$ phonegap serve (and use the PhoneGap Developer App), or
-
$ phonegap run [ios|android] [--device]
~ or ~
-
Open the PhoneGap Developer App and point it at: http://take.pixfor.me:8888
-
Source on the USB sticks the assistants have…
‘ OR 1=1; --
SQL Injection
Little Bobby Tables
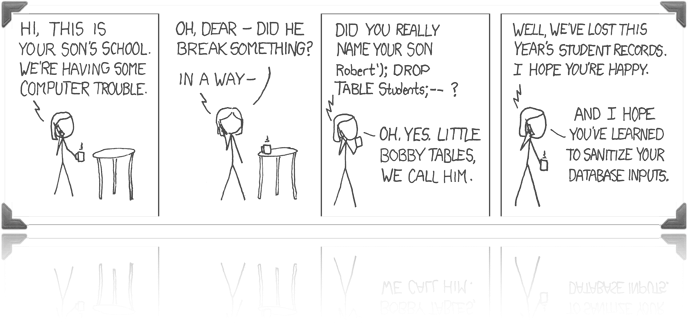
Robert’; DROP TABLE Students; --
Let's try it...
What Can We Do?
SQL Injection
If nothing else...
-
Avoid SQL injection by use of parameterisation
-
This keeps untrusted input from breaking out of the parameter context
-
-
And of course, listen to Bobby’s mom and sanitise your inputs
XSS
Cross Site Scripting
Is XSS that big of a deal?
ಠ_ಠ
Two Primary concerns
-
What are the sources of input?
-
Where is this data going (the target)?
Sources
-
Location and URL Sources
-
Cookies
-
Referrer (less so in a PhoneGap app)
-
Window Name
-
Indirect Sources (Client side db such as sqlite/pouch/etc)
-
Other Objects (Post Message/Intents/etc)
Targets
-
Execution Target
-
HTML Element Target
-
Set Location Target
-
Control Flow Target
-
…and more
-
eval()
-
onclick, onsubmit, …
-
Function()
-
script.src
-
setTimeout()
-
script.text
-
setInterval()
-
script.textContent
-
setImmediate()
-
script.innerText
-
etc…
Execution Target
HTML Element Target
-
document.write
-
document.writeln
-
element.innerHTML
-
element.insertAdjacentHTML
-
Range.createContextualFragment
-
HTMLButton.value
-
.append() (jQuery and friends)
-
etc...
Set Location Target
-
window.location
Control Flow Target
-
this[foo](bar)
-
seems contrived, but allows arbitrary script execution if input `foo` is untrusted
-
A Quick Note About
Frameworks
Problems With Frameworks
-
Add complexity
-
Abstract away targets (innerHTML, etc)
-
Add syntactic sugar
-
Add loopholes to browser security controls
-
The frameworks and practices you use should (attempt to) be secure by default
-
If your frameworks add syntactic sugar, be aware of the implications
jQuery
-
jQuery is practically a target in and of itself (mostly fixed)
-
be aware that old versions might be targets
-
-
Full of HTML element targets:
-
$(el).add(userContent)
-
$(el).append(userContent)
-
$(el).after(userContent)
-
$(el).html(userContent), etc…
-
Angular
-
Old versions should be avoided and updated
-
1.1.5? <div class=“ng-app"> {{constructor.constructor('alert(1)')()}} </div>
-
Fixed now, but beware older versions
-
React
-
Gives a clue in the function name:
-
dangerouslySetInnerHTML()
-
but devs still use it (static site generators, etc)
-
-
Not using it also doesn’t alleviate the need to sanitise your inputs
Stay 👏 Up 👏 To 👏 Date 👏
This applies to PhoneGap/Cordova and its plugins as much as your front-end JavaScript frameworks
What Can We Do?
Cross Site Scripting (XSS)
Minimise Attack Surface
-
Avoid converting strings to scripts
-
Avoid innerHTML wherever possible!
-
Don't write your own HTML sanitiser (srsly)
-
Whitelist*
-
Content Security Policy (CSP)*
* we’ll get to these in a bit
Avoid Converting Strings To Scripts
-
eval, Function.apply, setTimeout("string")
-
inline event handlers
-
onclick="string"
-
-
etc
Avoid innerHTML Wherever Possible
-
.textContent
-
$(el).text()
-
document.createElement/setAttribute
-
Use a template system with escaping
-
HOWEVER!! location targets are not as protected i.e.:
-
<a href="{{value}}">...</a>
-
-
Try Not To Write Your Own HTML Sanitiser
-
If you MUST…
-
Whitelist, NOT blacklist
-
fail conservatively
-
better to fail to display nicely than to be insecure
-
-
instead consider:
-
DOMPurify, Angular's $sanitize, Bleach.js (for workers?), etc…
-
TL;DR
-
Avoid eval & innerHTML
-
Use a template lang* with escaping, but be careful with attributes
-
filter HTML input conservatively
-
Whitelist / CSP
* A lot of the tempting languages don’t play well with CSP
Let's try it...
Next, Maybe Some Fun To Make Sure You Are
AWAKE
Do You Recognise Any Of These?
1F, 4A1564, 4F, 68 Middle Street, 6ikauoa1, 802AA85904AF, 9479FF763F6F, A7526EC772FA, ADYa2V2bzY1, ALAN, APARTAMENTOS VIVELO, AdobeCorp, AdobeGuest, Airplay, Airport_Free_WiFi, Airport_Paid_Premium_WiFi, Amasdam, AmexEvents, B, BEL-AMI, BJNPSETU6, BJNPSETUP, BTOpenzone-B, BTWi-fi, BTWifi-with-FON, CASA CH, CRITEO_CORP, CRITEO_Guest, CRITEO_MyDevices, CROSS, Chromecast MH, ClickDealer, Crowne Plaza, DK088A, De_Zwijger, Derma2Care_RB380, DeutschGuest, DowntownBrooklynWifi_Fon, Droidcon, European Athletics 2016, F, FINCHFACTOR, FON_BELGACOM, FON_ZON_FREE_INTERNET, Gatwick FREE Wi-Fi, H369A261989, H369ADCF905, HSGUEST, HZN246910305, IC Conference Room, ILLYGUEST, InfostradaWi j-ae222a, InfostradaWiFi-ae222a, InfostradaWiFi-f1a522, InterContinental, Intercontinental, KPN, KPN Fon, KW Hotel, Keizers, Kerkstraat 142, Liveperson, MBUGGUSS, MOB HOTEL, MOBIKIT-HUB, MOBIMENTUM_5G, Members_Herengracht, Michael Home, MirkoNet2G, MirkoNet5G, Modera Wireless, Mothership, N, Nilth2010, NogEenMod, O2 Wifi, O2 Wifi.1x, OTE WiFi Fon, Office-WORK, OpenSourceSummit, Ordina Guest, PARC55-GUESTROOM, PASCHKE_CA, PLUSNET-HKXF, PR-GAST, PV-Elze, Personal, Phian, PhoneGap, Public, Publiek_Herengracht, Radisson_Guest, Rocksteady Network, Rush Hour FMz, SHTMobileDevice, STARBUCKS_AIS, SX551DDA153, Seats2meet.com snelst, Sheraton_GUEST, Sitecom46B967, Solid Attendees, SpotcapNL, Spotify-Guest, SternHotspot, Streamyx Mobility, Swisscom, TELE2-E9308D, TELENETHOTSPOT, THALYSNET, TJR 008, TP-LINK_6DD8, TTNET WiFi Fon, Telekom, Telekom Fon, Telekom_FON, Telstra Air, The Mood, TheMachine, Tidewater B, UPC0042475, UPC2252314, UPC249522708, Villa Odyssea, Vince 2.0, VodafonU6WifiUrs, Vodafone NL Wifi, Vodafone-Laura, Vodafone-WifiUrs, Vught-Gastennetwerk, WLAN-PUB, WWGuest, Wifi+, ZXHNH369A, ZazaStudio, ZazaStudio-5G, Ziggo3964683, Ziggo84898, Ziggo9CA370, Zonheuvel Algemeen, Zy_private_JFTMQS, _Summit2017, _The Cloud X, bagelsenbeans, bedfordfree, casa del cielo 5ghz, dsmgast, fazidin2, h369ADCF905, hackerzentrale, hhonors, iPhone, iPhone di Giosue, island-113F90, linksys, mdtmobile, mwbrooks-5ghz, net+ Fon, o2-WLAN54, projekt rk Gastzugang, publiek_herengracht, publiek_vijzel, telenet-F7E358E, vinUrs, zulkefley13@unifi, Wifi Extra
Your devices are always looking for Wifi they know
-
These are called “Probe Requests”
-
If the WiFi was unencrypted (no WEP/WPA, etc), then another device could see these probe requests and simply pretend to be that WiFi (i.e.: A WiFi Pineapple, etc)
-
Most devices would then happily join and start sending traffic through the malicious WiFi spot
-
Even easier is a “honey pot” like a WiFi called “FREE WIFI”, etc. Everyone likes free WiFi.
These are just some of the many ways to become a:
Man in the Middle
(MitM)

Maybe It's Time For A Quick
Demo
Let me introduce you to mitmproxy...
What Can We Do?
Man in the Middle (MitM)
All Of Them
Yes...

Too Hard? Too Expensive?
CSP
Content Security Policy
What is it?
-
It’s a whitelist of content sources
-
All official PhoneGap and Cordova templates include a CSP
<meta http-equiv="Content-Security-Policy"
content="default-src * data: gap: 'unsafe-inline';
style-src 'self' 'unsafe-inline';
media-src *" />
<meta http-equiv="Content-Security-Policy"
content="default-src 'self' data: gap:
https://ssl.gstatic.com
https://mysite.com;
object-src *;
style-src 'self' data: 'unsafe-inline';
img-src 'self' data:;
media-src 'self' data: https://mysite.com:8888;
font-src 'self' data:; connect-src *">
Basic
A bit more...
PhoneGap Specific
OK. Let's Get More
Cordova Whitelist
cordova-plugin-whitelist
<!-- Allow images, xhrs, etc. to mysite.com -->
<access origin="http://mysite.com" />
<allow-navigation href="http://mysite.com/*" />
<allow-intent href="http://*/*" />Read And Understand The Whitelist Guide
-
<access origin=“https://*.mydomain.com" /> -
On iOS:
-
Application Transport Security (ATS)
-
<access origin="https://*.mydomain.com" minimum-tls-version="TLSv1.1" requires-forward-secrecy="false" />
-
iFrames
The Problem With
Access To "The Bridge"
-
Can have access to the native Cordova bridge
-
e.g.: third-party advertising network served through an iframe
-
Be careful what you whitelist!
Certificate Pinning
Getting Advanced With
(Limited) Options For Pinning
-
Cordova does not support true certificate pinning
-
There are ways to approximate certificate pinning
-
T.O.F.U. (yum)
-
EddyVerbruggen/SSLCertificateChecker-PhoneGap-Plugin
-
-
True certificate pinning for some platforms
Some More Advice From The Security Guide
-
Do not use Android Gingerbread (2.3)!
-
Use InAppBrowser for outside links
-
Validate all user input (worth repeating)
-
Do not cache sensitive data
-
Don't use eval() unless you know what you're doing
-
Do not assume that your source code is secure
Resources
- OWASP Top 10
- SQL Injection Myths and Fallacies
- PhoneGap Platform Security wiki
- Online Security Confs
- XSS (Cross Site Scripting) Prevention Cheat Sheet
- HTML4 Security Cheat Sheet
Tommy-Carlos Williams
Thanks!
Privacy and Security for PhoneGap developers
By devgeeks
Privacy and Security for PhoneGap developers
- 1,515





